45 aws security best practices
AWS Security Best Practices - AWS Security Best Practices AWS Security Best Practices. AWS Whitepaper. Welcome; AWS Documentation AWS Whitepapers AWS Whitepaper. AWS Security Best Practices. PDF RSS. Notice: This whitepaper has been archived. For the latest technical information on ... Security best practices in IAM - AWS Identity and Access … Jul 14, 2022 · Use the root user to complete the tasks that only the root user can perform. For the complete list of these tasks, see Tasks that require root user credentials in the AWS General Reference. For more information, see Best practices to protect your account's root user in the AWS Account Management User Guide.
AWS Security Best Practices Amazon Web Services AWS Security Best Practices Page 1 Introduction Information security is of paramount importance to Amazon Web Services (AWS) customers. Security is a core functional requirement that protects mission- critical information from accidental or deliberate theft, leakage, integrity compromise, and deletion.

Aws security best practices
AWS Cloud Security: Top Risks, Best Practices, & Tools AWS cloud security best practices are those steps that enhance the available security within the AWS cloud when taken. These solutions include: Data Encryption; Encryption is quite important to keep data that is stored and transmitted in the cloud secure from malicious attacks. It is also a security mandate for some regulatory standards without ... Security best practices in AWS CloudTrail - AWS CloudTrail CloudTrail detective security best practices. Create a trail. For an ongoing record of events in your AWS account, you must create a trail. Although CloudTrail provides 90 days of event history information for management events in the CloudTrail console without creating a trail, it is not a permanent record, and it does not provide information about all possible types of events. Best Practices - Security - Amazon Elastic Container Service Best Practices - Security This guide provides security and compliance recommendations for protecting your information, systems, and other assets that are reliant on Amazon ECS. It also introduces some risk assessments and mitigation strategies that you can use to have a better grip on the security controls that are built for Amazon ECS clusters and the workloads that they support.
Aws security best practices. What is DevOps? - Amazon Web Services (AWS) DevOps is the combination of cultural philosophies, practices, and tools that increases an organization’s ability to deliver applications and services at high velocity: evolving and improving products at a faster pace than organizations using traditional software development and infrastructure management processes. docs.aws.amazon.com › security-best-practicesSecurity Best Practices for Amazon S3 Amazon S3 provides a number of security features to consider as you develop and implement your own security policies. The following best practices are general guidelines and don’t represent a complete security solution. Getting Started: Follow Security Best Practices as You Configure Your ... Jun 08, 2017 · Introduction to AWS Security whitepaper; AWS Cloud Security Resources; AWS Security Best Practices whitepaper; Security by Design; If you have comments about this post, submit them in the “Comments” section below. If you have questions about or issues implementing these best practices, please start a new thread on the IAM forum. – Andy Aws security best practices white paper työt - Freelancer Etsi töitä, jotka liittyvät hakusanaan Aws security best practices white paper tai palkkaa maailman suurimmalta makkinapaikalta, jossa on yli 21 miljoonaa työtä. Rekisteröityminen ja tarjoaminen on ilmaista.
AWS Security Best Practices - Rivia AWS Certified Solutions Architect -Associate Exam (SAA-002) 0% Complete. 0/0 Steps . Course Contents. 2 Lessons Section 1: AWS Exam. 3 Lessons ... Domain 3 - Design Secure Applications and Architectures AWS Security Best Practices. In Progress. Module 5, Lesson 4. In Progress. Security Best Practices for Amazon S3 Enable AWS Config. Several of the best practices listed in this topic suggest creating AWS Config rules. AWS Config enables you to assess, audit, and evaluate the configurations of your AWS resources. AWS Config monitors resource configurations, allowing you to evaluate the recorded configurations against the desired secure configurations ... aws.amazon.com › blogs › securityGetting Started: Follow Security Best Practices as You ... Jun 08, 2017 · Introduction to AWS Security whitepaper; AWS Cloud Security Resources; AWS Security Best Practices whitepaper; Security by Design; If you have comments about this post, submit them in the “Comments” section below. If you have questions about or issues implementing these best practices, please start a new thread on the IAM forum. – Andy AWS VPC Security: 13 Best Practices [The 2022 Guide] - Hyperglance The best practice is to split your production, staging, and pre-production environments across different VPCs. Image courtesy of AWS 5. Use Security Groups To Control Resource Access It's vital that you factor in AWS Identity Access Management (IAM) when you're planning and setting up your VPC.
AWS Foundational Security Best Practices standard The AWS Foundational Security Best Practices standard is a set of controls that detect when your deployed accounts and resources deviate from security best practices. The standard allows you to continuously evaluate all of your AWS accounts and workloads to quickly identify areas of deviation from best practices. Security best practices for Amazon EKS - Amazon EKS Amazon EKS security best practices are maintained on Github: PDF AWS Security Best Practices - AWS Whitepaper Title: AWS Security Best Practices - AWS Whitepaper Author: Amazon Web Services Created Date: 20220728224323Z Learn best practices for securing your AWS account and resources Sep 18, 2020 · You can contact AWS Support with questions about your account's activity. However, for privacy and security reasons, AWS doesn't actively monitor your usage and uses limited tools to investigate issues. It's a best practice to actively monitor your account and its resources to detect any unusual activity or access to your account.
docs.aws.amazon.com › IAM › latestSecurity best practices in IAM - AWS Identity and Access ... Jul 14, 2022 · Use the root user to complete the tasks that only the root user can perform. For the complete list of these tasks, see Tasks that require root user credentials in the AWS General Reference. For more information, see Best practices to protect your account's root user in the AWS Account Management User Guide.
PDF ARCHIVED: AWS Security Best Practices This whitepaper describes best practices that you can leverage to build and define an Information Security Management System (ISMS), that is, a collection of information security policies and processes for your organization's assets on AWS. For more information about ISMSs, see ISO 27001 at .
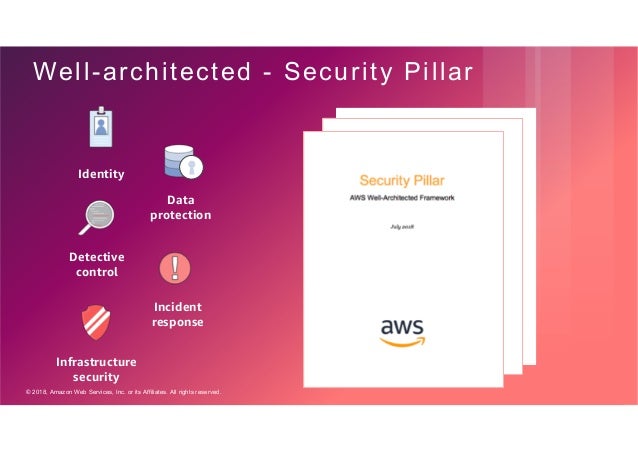
AWS Security Best Practices - CoreStack Introduction - AWS Security Best Practices. AWS provides its users with a wide variety of managed security services, as well as security guidelines and patterns. When followed, these services help ensure that your business can meet any regulatory requirement. In fact, security forms one of the six pillars of the "AWS Well-Architected Framework". This framework is designed to help compare your infrastructure against industry best practices and identify any weaknesses or areas for ...
AWS Cloud Security: Best Practices for Financial Services It is possible to enhance AWS Cloud Security by just following a few security best practices defined below: 1. Establish an Effective Governance Strategy In a multi-cloud environment, utilize AWS Control Tower to build in security guardrails that enforce your organizational policies and remain in effect as you create new accounts or make changes to existing accounts. 2.
aws.amazon.com › security-best-practicesLearn best practices for securing your AWS account and resources Sep 18, 2020 · You can contact AWS Support with questions about your account's activity. However, for privacy and security reasons, AWS doesn't actively monitor your usage and uses limited tools to investigate issues. It's a best practice to actively monitor your account and its resources to detect any unusual activity or access to your account.
docs.aws.amazon.com › best-practices-securitySecurity best practices in AWS CloudTrail - AWS CloudTrail CloudTrail detective security best practices. Create a trail. For an ongoing record of events in your AWS account, you must create a trail. Although CloudTrail provides 90 days of event history information for management events in the CloudTrail console without creating a trail, it is not a permanent record, and it does not provide information about all possible types of events.
Cloud Security – Amazon Web Services (AWS) With AWS, you control where your data is stored, who can access it, and what resources your organization is consuming at any given moment. Fine-grain identity and access controls combined with continuous monitoring for near real-time security information ensures that the right resources have the right access at all times, wherever your information is stored.
AWS Cloud Security Best Practices | CrowdStrike To harden your security even more, you can rotate these external IDs once in a while. Keep Your Policies Simple, Small, and Scalable. You know AWS uses policies to grant or prevent access of principals to resources. This is how you should define who gets access to what, according to AWS.
AWS Security Best Practices Checklist | CDWG By discussing common security threats and questions with employees, you can make them feel more comfortable with AWS services. The greater an employee's knowledge of security services, the better they will be protected—and having a company culture based on cybersecurity helps to provide those benefits. 7. Maintain Regulatory Compliance
Top 10 security items to improve in your AWS account Mar 20, 2020 · AWS Security Hub, Amazon GuardDuty ... Review best practices for managing AWS access keys for more guidance. If your users access AWS via federation, then you can remove the need to issue AWS access keys for your users. Users authenticate to the IdP and assume an IAM role in the target AWS account. The result is that long-term credentials are ...
Best Practices | AWS Security Blog Introducing the AWS Best Practices for Security, Identity, & Compliance Webpage and Customer Polling Feature. The AWS Security team has made it easier for you to find information and guidance on best practices for your cloud architecture. We're pleased to share the Best Practices for Security, Identity, & Compliance webpage of the new AWS Architecture Center.
AWS Security Best Practices | Classroom Training | AWS The AWS Security Best Practices course will help you learn to design and implement solutions to keep your workloads safe and secure. Through presentations, demonstrations, and hands-on lab you will dive deep into configuration best practices for specific tools to secure your network infrastructure, harden your compute resources, and quicken your response to suspicious events.
docs.aws.amazon.com › whitepapers › latestAWS Security Best Practices - AWS Security Best Practices AWS Security Best Practices. AWS Whitepaper. Welcome; AWS Documentation AWS Whitepapers AWS Whitepaper. AWS Security Best Practices. PDF RSS. Notice: This whitepaper has been archived. For the latest technical information on ...
9 AWS Security Best Practices - Alert Logic [ Data Security Best Practices] 6. Backup Your Data You never know if you're going to need to restore data after a breach, so back up your data regularly. You can do this by using AWS Backup. This app makes it easy to automate backups across your AWS environment, so you never have to worry about losing important information.
AWS Security Best Practices | Cyphere - thecyphere.com AWS Security Best Practices. Using security best practices helps businesses establish a security baseline and protect their AWS infrastructure from potential risks. By implementing these practices, companies can reduce the likelihood of data breaches, leaks, and other threats. Additionally, using security best practices can help businesses detect and respond to threats more quickly and effectively.
d1.awsstatic.com › AWS_Security_Best_PracticesAWS Security Best Practices Amazon Web Services AWS Security Best Practices Page 1 Introduction Information security is of paramount importance to Amazon Web Services (AWS) customers. Security is a core functional requirement that protects mission- critical information from accidental or deliberate theft, leakage, integrity compromise, and deletion.
13 AWS Security Best Practices - Check Point Software By following this AWS security best practices checklist, it is possible to improve the security of an AWS deployment. Identify Security Requirements 1. Define and Categorize Assets in AWS: It is impossible to secure systems that you don't know exist.
AWS Security Best Practices in 11 Steps - Apexon Step 1: Understand the Shared Responsibility Model. Amazon's responsibility: AWS is focused on infrastructure security, including computing, storage, database, and intrusion prevention networking services. AWS is also responsible for the security of the software, hardware, and the physical facilities that host AWS services.












0 Response to "45 aws security best practices"
Post a Comment